Summary
- Security scans can’t detect BingoMod reliably, but it is a new Android malware that can steal your money.
- The malware is presently targeting Italian devices, hiding behind fake notifications and stolen app identities.
- Avoid smishing by never clicking links from unverified sources.
Malware has been the bane of everyone’s online existence, because it serves as the easiest back-door entry for perpetrators of cybercrime and thievery. Google is usually on its toes, keeping the Play Store free of nefarious apps and ensuring prompt delivery of Android security patches, but some attackers manage to stay ahead of the curve and still steal money or personal information from victims. One such malware was recently caught in the wild targeting Android devices, stealing all financial data on them, and then wiping them clean.
Related
What to do if you accidentally click on a phishing link
Don’t panic, you can still keep your data secure
Android malware dons several cloaks, but the latest one to stay wary of is called BingoMod, and Bleeping Computer found a report from researchers at cybersec firm Cleafy saying it uses a technique called smishing to attack devices (via WinFuture). Smishing, or SMS phishing delivers a malware-laced weblink to the unsuspecting victim’s device, which in this case installs the BingoMod app (version 1.5.1) under a false identity, usually spoofing the app name and icon for mobile security tools like AVG AntiVirus & Security.
During installation, the app requests access to device accessibility services, which it leverages to steal login credentials, take screenshots, and intercept SMS messages. All this is also sent to the threat actor via a dedicated channel, giving them near real-time access to the device’s functions. Cleafy also reports the malware relies on Android’s media projection APIs responsible for handling screencasting requests, to gather the displayed information, which helps bad actors circumvent security measures like 2FA authentication.
Targeting devices in Italy while in active development
Source: Cleafy
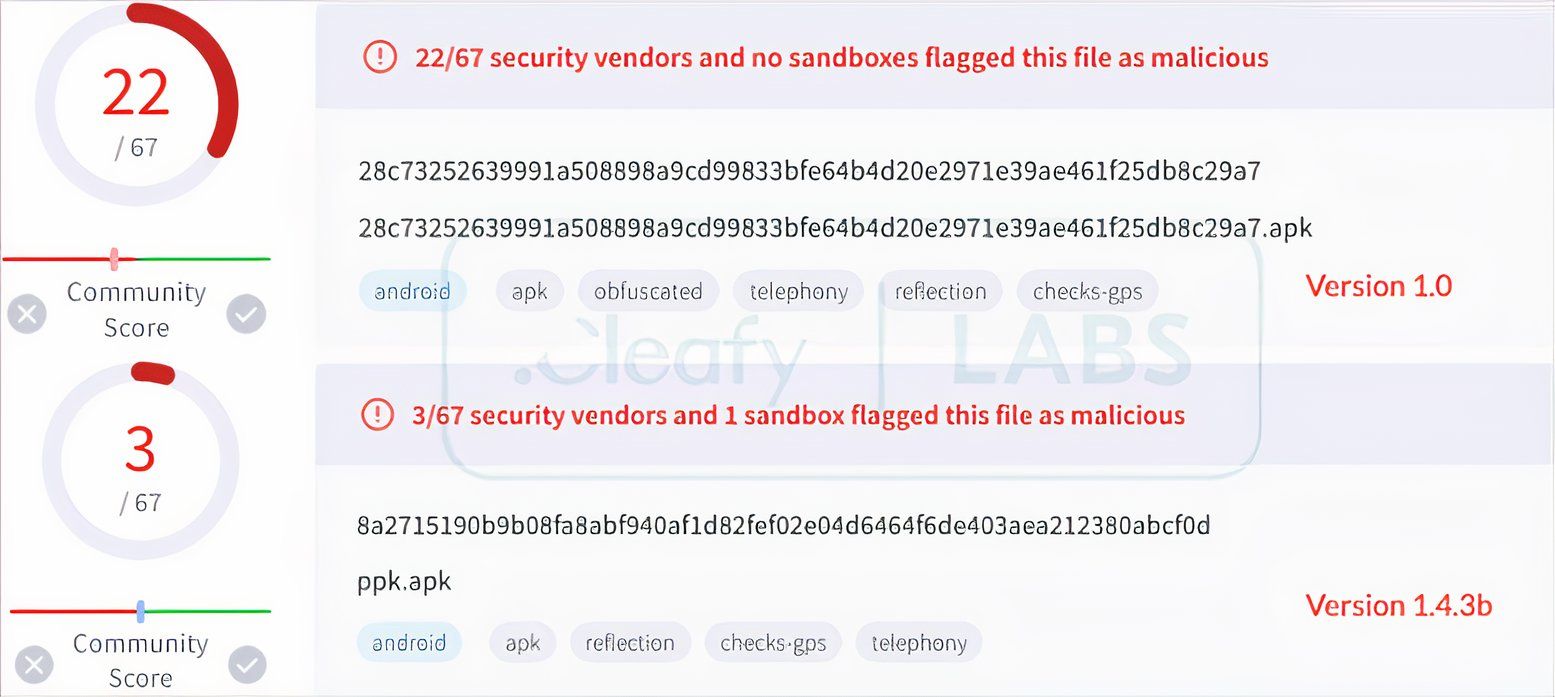
Security scans can’t detect BingoMod reliably
BingoMod is currently concealing its attacks from the victims using fake notifications and other overlays on the screen while stealing money and data in the background. The app is believed to be of Romanian origin with potential contribution of developers from other parts of the world, and is currently targeting devices in Italy, stealing as much as 15,000 Euros in every transaction. However, experts at Cleafy worry the malware could target devices in other markets too, since the app is in active development.
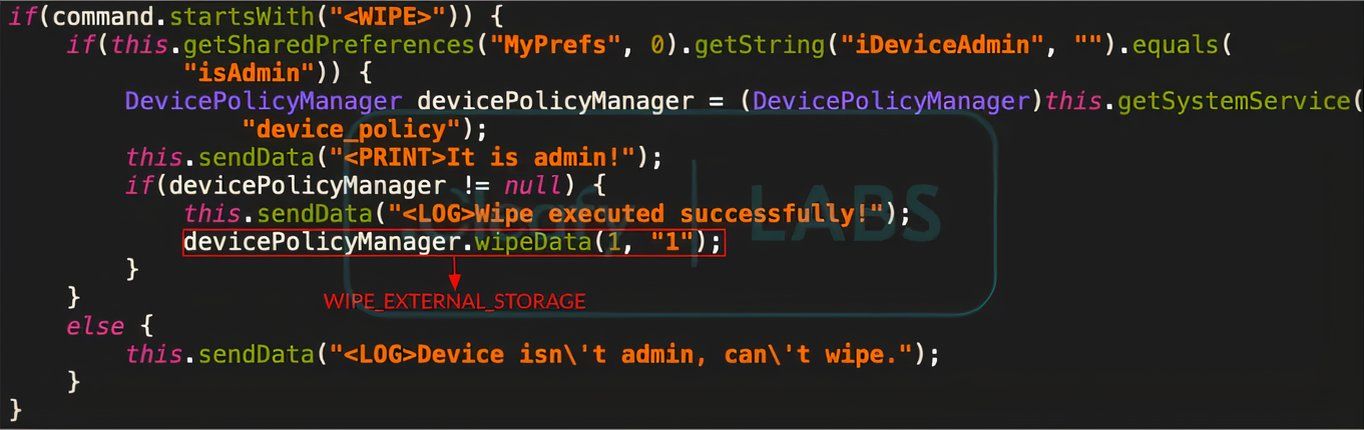
BingoMod’s evasive techniques are already helping the app avoid detection by well-regarded tools like VirusTotal, and the infected device can further infect more devices too. In case the victim gives the BingoMod app device administrator privileges, the bad actors can remotely wipe the device too, although Cleafy says it would only clean out the attached external storage.
Source: Cleafy
BingoMod code confirms its ability to wipe the targeted device
As always, the best way to steer clear of such smishing attacks is to never click links from unverified sources, especially those claiming to be important. Prefer installing apps from reputable sources like the Google Play Store, and set up passkeys whenever possible, so your online accounts have a layer of biometric security too. Lastly, use one of our favorite password managers to keep your credentials safe and be warned of recent data breaches which could leave your accounts compromised.